|
|
Compare and contrast the hash algorithms used in PGP and S/MIME.
This question has 0 answers so far.
|
|
|
Explain how does tunnel mode provide protection to the IP Packets.
This question has 0 answers so far.
|
|
|
Find greatest common divisor of 161 and 28 by using Extended Euclidean Algorithm.
This question has 0 answers so far.
|
|
|
Define the Codes.
This question has 0 answers so far.
|
|
|
Define the Ciphers.
This question has 0 answers so far.
|
|
|
Define the Confusion.
This question has 0 answers so far.
|
|
|
Define the Diffusion.
This question has 0 answers so far.
|
|
|
Explain Hill Cipher Technique by taking a suitable example.Discuss any two disadvantages of Hill Cipher Technique.
This question has 0 answers so far.
|
|
|
Briefly discuss Differential Cryptanalysis Attack in DES.
This question has 0 answers so far.
|
|
|
Give a detail description of single round of DES algorithm.
This question has 0 answers so far.
|
|
|
Explain the steps in Playfair Cipher technique.
This question has 0 answers so far.
|
|
|
Explain Diffie Hellman key exchange and explain how does it suffer from Man-in-Middle attack.
This question has 0 answers so far.
|
|
|
Explain Time Domain and Frequency Domain Scramblers.
This question has 0 answers so far.
|
|
|
Perform the encryption and decryption of the plain text, M-8, where recipients RSA public key are (0-77,c-17).
This question has 0 answers so far.
|
|
|
Briefly explain Elliptic curve cryptography.
This question has 0 answers so far.
|
|
|
Explain the Digital Signature Standard (DSS) approach to digital signatures.
This question has 0 answers so far.
|
|
|
What are some weaknesses of a Packet - filtering router.
This question has 0 answers so far.
|
|
|
Explain the various steps involved in the Secured Socket Layer(SSL) Record Protocol transmission.
This question has 0 answers so far.
|
|
|
Discuss, Oakley Key Determination Protocol in IPSec.
This question has 0 answers so far.
|
|
|
Explain in detail the TMN Architecture.
This question has 0 answers so far.
|
|
|
Briefly explain TMN management service architecture.
This question has 0 answers so far.
|
|
|
Discuss some implementation issues of TMN
This question has 0 answers so far.
|
|
|
Write the algorithm to compute xy mod z for very large values of x and y.
This question has 0 answers so far.
|
|
|
Differentiate between passive and active attacks. Name some passive attacks.
This question has 0 answers so far.
|
|
|
What are the characteristics of a secure hash function?
This question has 0 answers so far.
|
|
|
Define the Brute force attack Terms briefly.
This question has 0 answers so far.
|
|
|
Define the Replay attack Terms briefly.
This question has 0 answers so far.
|
|
|
Define the Differential Cryptanalysis attack Terms briefly.
This question has 0 answers so far.
|
|
|
Discuss how does DES use the Initial Permutation concepts.
This question has 0 answers so far.
|
|
|
Discuss how does DES use the Final Permutation concepts.
This question has 0 answers so far.
|
|
|
Discuss how does DES use the S-box concepts.
This question has 0 answers so far.
|
|
|
Discuss how does DES use the XOR operation concepts.
This question has 0 answers so far.
|
|
|
Discuss how does DES use the Round key generator concepts.
This question has 0 answers so far.
|
|
|
Discuss the Difference between Stream Cipher and Block Cipher.
This question has 0 answers so far.
|
|
|
Discuss the Difference between Substitution Technique and transposition technique.
This question has 0 answers so far.
|
|
|
Discuss the Difference between Electronic Code book Mode and Cipher Block Chaining Mode.
This question has 0 answers so far.
|
|
|
Explain the key Generation and Encryption / Decryption Process of RSA algorithm. Explain the RSA based digital Signature Mechanism.
This question has 0 answers so far.
|
|
|
Explain how do Alice (sender) and Bob (Recipient) get the same keyin a -insecure channel by Using Diffie Hellman key exchange algorithm. Explain limitation of Diffie-Hellman Scheme.
This question has 0 answers so far.
|
|
|
Differentiate between Time Domain and Frequency Domain Scramblers.
This question has 0 answers so far.
|
|
|
Explain how does PGP incorporates the Confidentiality security leatures.
This question has 0 answers so far.
|
|
|
Explain how does PGP incorporates the Integrity security leatures.
This question has 0 answers so far.
|
|
|
Explain how does PGP incorporates the Authentication security leatures.
This question has 0 answers so far.
|
|
|
Explain how does PGP incorporates the Compression security leatures.
This question has 0 answers so far.
|
|
|
Explain How does IPsec manage to counter Replay attack?
This question has 0 answers so far.
|
|
|
Discuss the various processes involved in SHA-512.
This question has 0 answers so far.
|
|
|
Explain in detail the TMN Functional Architecture and Informational Architecture.
This question has 0 answers so far.
|
|
|
Write Notes on Firewall design Principle.
This question has 0 answers so far.
|
|
|
Write Notes on TMN Reference Point.
This question has 0 answers so far.
|
|
|
Write Notes on TMN services.
This question has 0 answers so far.
|
|
|
a. With a neat diagram, explain network access security model with gate keeper function.
This question has 0 answers so far.
|
|
|
b. Classify and explain different type of attacks.
This question has 0 answers so far.
|
|
|
c. Using the keyword "ENCRYPT" create playfair matrix and obtain ciphertext for the message "MATCHFIXED". Also write the rules used.
This question has 0 answers so far.
|
|
|
a. Explain single round of DES along with the key generation.
This question has 0 answers so far.
|
|
|
b. Explain the working of counter mode of block cipher operation.
This question has 0 answers so far.
|
|
|
c. Discuss the final evaluation criteria of AES.
This question has 0 answers so far.
|
|
|
a. Justify how both confidentiality and authentication are obtained in publickey cryprosystems.
This question has 0 answers so far.
|
|
|
b. Write RSA algorithm.
This question has 0 answers so far.
|
|
|
c. In Diffie Hellman key exchange q = 71, its primitive root 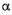 = 7 A's private key is 5 B's
private key is 12. Find: i) A's public key; ii) B's public key, iii) Shared secret key. = 7 A's private key is 5 B's
private key is 12. Find: i) A's public key; ii) B's public key, iii) Shared secret key.
This question has 0 answers so far.
|
|
|
d. Explain the distribution of secret key using the public key cryprography with confidentiality and authentication.
This question has 0 answers so far.
|
|
|
a. List out the requirements and explain the arbitrated digital signature technique.
This question has 0 answers so far.
|
|
|
b. Compare RSA and DSS approach.
This question has 0 answers so far.
|
|
|
c. Illustrate replay attack with examples.
This question has 0 answers so far.
|
|
|
a. Explain the key requirements and features of SET.
This question has 0 answers so far.
|
|
|
b. Discuss SSL record in terms of fragment compression and encryption.
This question has 0 answers so far.
|
|
|
a. Explain password selection strategies.
This question has 0 answers so far.
|
|
|
b. Describe statistical anomaly detection.
This question has 0 answers so far.
|
|
|
c. Discuss the different categories of intruders.
This question has 0 answers so far.
|
|
|
a. Give the taxonomy of malicious programs, Briefly explain all the software threats.
This question has 0 answers so far.
|
|
|
b. Describe digital immune system with diagram.
This question has 0 answers so far.
|
|
|
c. Brief on four generations of Antivirus software.
This question has 0 answers so far.
|
|
|
a. What is firewall? Explain the various firewall configurations with relevant diagram.
This question has 0 answers so far.
|
|
|
Write short note on: i) Data Access Control
This question has 0 answers so far.
|
|
|
Write short note on: ii) Concept of Trusted system
This question has 0 answers so far.
|
|
|
What are the basic requirement of Secure Electronic Transaction?
This question has 0 answers so far.
|
|
|
What are the two basic components of the network security model?
This question has 0 answers so far.
|
|
|
Explain any four functions of S/MIME.
This question has 0 answers so far.
|
|
|
Mention the significance of a trup-door one way key functio in public encryption systems.
This question has 0 answers so far.
|
|
|
Compare the characteristics of Link and End-to-End Encryption schemes.
This question has 0 answers so far.
|
|
|
Define steganography?What are various technique used in steganography?
This question has 0 answers so far.
|
|
|
Define the features of Stream ciphers with an example.
This question has 0 answers so far.
|
|
|
What in the difference between direct and arbitrated digital signatures?
This question has 0 answers so far.
|
|
|
What are the essential ingredients of a public-key directory?
This question has 0 answers so far.
|
|
|
On the elliptic curve over the real numbers Y2x3 -36x, let (-3.5.9.5) and Q=(-2.5, 8.5). Find P+Q and 2P.
This question has 0 answers so far.
|
|
|
What is the purpose of the X.509 standard and how is an X.509 certificate can be revoked?
This question has 0 answers so far.
|
|
|
In PGP'scheme, what is the expected number of session key generated before a previously created session key is produced? Wat is the probability that a user with N public keys will have at least of duplicate key ID?
This question has 0 answers so far.
|
|
|
What is the difference between Secure Sockets Layer (SSL Connection and SSL session? Explain.
This question has 0 answers so far.
|
|
|
Explain the functioning of Telecommunications Management network(TMN) layers.
This question has 0 answers so far.
|
|
|
How does TMN information model provide security management?Explain.
This question has 0 answers so far.
|
|
|
Explain the functioning of a digital immune system? Give an instration,
This question has 0 answers so far.
|
|
|
What is IP Spoofing? Explain the vulnerabilities.
This question has 0 answers so far.
|
|
|
Explain authentication and non-repudiation.
This question has 0 answers so far.
|
|
|
Explain the dimensions and approaches of cryptogphy and cryptanalysis.
This question has 0 answers so far.
|
|
|
Explain briefly the types of Block Cipher Modes and their typical applications.
This question has 0 answers so far.
|
|
|
Compare and contrast Caesar cipher and Playfair cipher.
This question has 0 answers so far.
|
|
|
Write short notes on Firewalls.
This question has 0 answers so far.
|
|
|
Write short notes on Security characteristics of OSI architecture.
This question has 0 answers so far.
|
|
|
Write short notes on IP security architecture.
This question has 0 answers so far.
|
|
|
Write short notes on MIME.
This question has 0 answers so far.
|
|
|
Write short notes on DES and variants.
This question has 0 answers so far.
|
|
|
Attempt any five of the following: (a) Write a short note on Pretty Good Privacy (PGP).
(b) List four general categories of schemes for the distribution of public key,
(c) What are the roles of public key and private key?
(d) Write a short note on network management services,
(e)What is cryptanalysis? Differentiate between linear and differential
Cryptanalysis. (f)Explain playfair cipher substitution technique. What are its drawbacks?
(g) Explain the working of rotor machines.
This question has 0 answers so far.
|
|
|
List and briefly define types of cryptanalytic attacks based on what is known to attacker.
This question has 0 answers so far.
|
|
|
What is the difference between monoalphabetic cipher and a polyalphabetic cipher? Encrypt the plaintext wearecseitstudents using keyword deceptive.
This question has 0 answers so far.
|
|
|
Define the following terms with reference to DES - (i)Meet-in-the-middle attack
(ii)Key generation
(iii)Expansion/Permutation
(iv) S box
(v) Avalanche effect
This question has 0 answers so far.
|
|
|
Name various block cipher modes of operations. Explain output feedback mode in detail.
This question has 0 answers so far.
|
|
|
Explain the key generation and encryption/decryption process of RSA algorithm with example.
This question has 0 answers so far.
|
|
|
What is elliptic curve cryptography? How Diffie-Hellman key exchange algorithim implemented using elliptic curves?
This question has 0 answers so far.
|
|
|
How speech signals can be encrypted? Describe digital and analog system of speech encryption.
This question has 0 answers so far.
|
|
|
Define data compression. Differentiate between lossless and lossy compression.
This question has 0 answers so far.
|
|
|
Discuss, Oakley Key Determination Protocol in IPSec.
This question has 0 answers so far.
|
|
|
Explain SSL (Secure Socket Layer) protocol stack. What is the difference between SSL connection and SSL session?
This question has 0 answers so far.
|
|
|
Explain digital signatures. How arbitrated digital signature is better than direct digital signature?
This question has 0 answers so far.
|
|
|
What is a scrambler? What are the three types of inversions used in speech scrambler?
This question has 0 answers so far.
|
|
|
Describe the telecommunication network architecture and discuss TMN management layers.
This question has 0 answers so far.
|
|
|
Define (i) Components of network architecture (ii) Structure of management information (iii)Types of telecommunication network (iv) Management information model
This question has 0 answers so far.
|